Unlock the power of secure web development with OWASP Top 10 2023! Dive into the latest edition, equipping yourself with cutting-edge insights and strategies to fortify your digital assets against evolving cyber threats by top 10 questions!
History of OWASP Top 10
The OWASP Top 10 is a compilation of the Open Web Application Security Project (OWASP), an international non-profit organization devoted to the advancement of software security hearing.
The history of OWASP top 10 is given below:
Early Versions
First released in 2003, OWASP Top 10 has become the internationally recognized standard for web security. It is designed to increase awareness of web security vulnerabilities. It highlights issues such as cross-site scripting (XSS), SQL injection, and insecure authentication.
Evolution and Updates
Consider the changing landscape of web application security. Updates are based on developments in attack strategies, vulnerabilities, and feedback from security experts and the developer community. Continuous development and release.
Recent Versions
The last major update came in 2021 with the release of OWASP Top 10 2021. This release introduces changes such as the addition of new categories such as API Security, while also improving existing entries to better deal with today’s threats.
Purpose and Impact
It has many uses in the security community. It informs developers and organizations about security risks, helps prioritize security, and provides a framework for assessing web security. It also encourages collaboration and knowledge sharing among security professionals worldwide. play an important role.
As cyber threats continue to evolve, the OWASP Top 10 remains a valuable resource for creating effective and secure web applications.
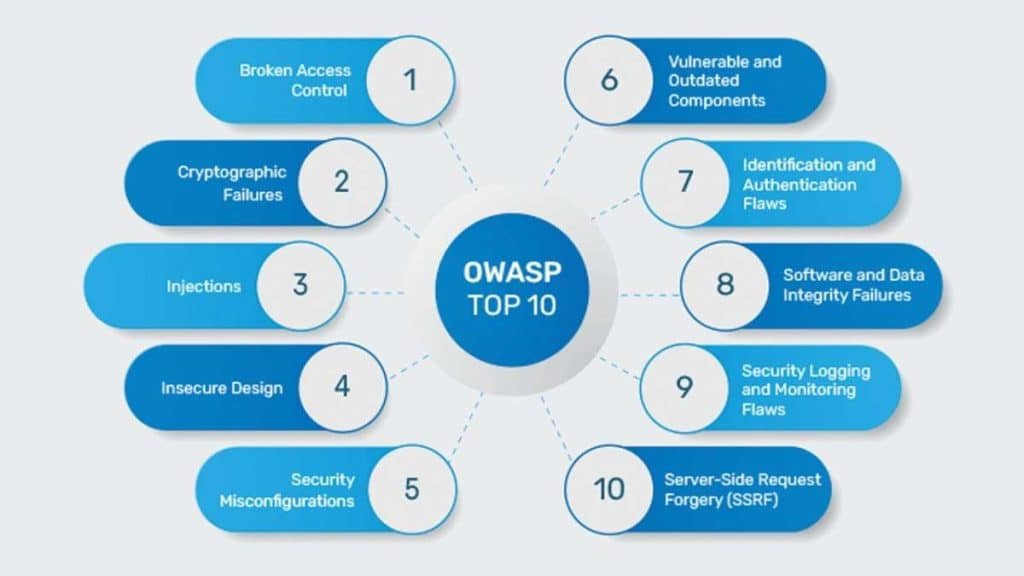
OWASP Top 10 Vulnerabilities
Regarding the topic Discover Vulnerabilities and Causes of OWASP Top 10 2023, here is OWASP top 10 vulnerabilities with their causes and details you must know:
- Injection
- Sensitive Data Exposure
- Broken Authentication
- XML External Entities (XXE)
- Broken Access Control (BAC)
- Security Misconfiguration
- Cross-Site Scripting (XSS)
- Insufficient Logging & Monitoring
- Insecure Deserialization
- Using Components with Known Vulnerabilities

| Vulnerabilities of OWASP 2023 | Causes | Details |
| Injection | Lack of input validation. Improper encoding/escaping of user input. Failure to use parameterized queries or prepared statements. | Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s malicious data can trick the interpreter into executing unintended commands or accessing unauthorized data. |
| Sensitive Data Exposure | Inadequate encryption. Improper storage of sensitive data, weak access controls. Lack of transport layer security (TLS). | Sensitive data exposure occurs when sensitive information, such as passwords, credit card numbers, or personal data, is not adequately protected. Attackers can steal or access this data through various means, leading to identity theft, fraud, or other malicious activities. |
| Broken Authentication | Weak password policies. Improper session management. Insecure storage of credentials. Lack of multi-factor authentication. | Broken authentication refers to vulnerabilities in authentication mechanisms, such as credential stuffing, brute force attacks, weak password policies, and session management flaws. Attackers exploit these weaknesses to gain unauthorized access to user accounts. |
| XML External Entities (XXE) | Inadequate encryption. Improper storage of sensitive data Weak access controls. Lack of transport layer security (TLS). | Sensitive data exposure occurs when sensitive information, such as passwords, credit card numbers, or personal data, is not adequately protected. Attackers can steal or access this data through various means, leading to identity theft, fraud, or other malicious activities. |
| Broken Access Control (BAC) | Improperly configured access controls. Insufficient authorization checks. Lack of proper session management. Direct object references. | Broken access control vulnerabilities occur when an application fails to properly enforce access controls, allowing unauthorized users to access restricted functionality or data. Attackers can exploit these flaws to escalate privileges, view sensitive information, or perform unauthorized actions. |
| Security Misconfiguration | Default configurations. Unnecessary services or features enabled. Lack of security hardening. Inadequate error handling. Improper permissions. | Security misconfiguration refers to insecure configurations of application components, frameworks, servers, or databases. These misconfigurations can expose sensitive data, provide unauthorized access, or facilitate other attacks. |
| Cross-Site Scripting (XSS) | Improper output encoding, failure to sanitize user input. Lack of content security policy (CSP). Reflective or stored XSS vulnerabilities. | Cross-Site Scripting (XSS) vulnerabilities occur when an application includes untrusted data in a web page sent to the browser without proper validation or escaping. Attackers can inject malicious scripts into the page, leading to various attacks, including session hijacking, defacement, or data theft. |
| Insufficient Logging & Monitoring | Inadequate logging of security-relevant events. Lack of log integrity checks, insufficient monitoring of system activities. Failure to establish clear incident response procedures. | Insufficient logging and monitoring refer to the lack of robust logging and monitoring capabilities in an application. Inadequate logging makes it difficult to detect and respond to security incidents, such as unauthorized access attempts, data breaches, or system compromises, in a timely manner. |
| Insecure Deserialization | Lack of input validation during deserialization. Use of insecure deserialization libraries. Unsafe deserialization of untrusted data. | Insecure deserialization vulnerabilities arise when an application deserializes untrusted data without proper validation or integrity checks. Attackers can exploit these flaws to execute arbitrary code, perform denial-of-service attacks, or tamper with application logic. |
| Using Components with Known Vulnerabilities | Failure to update or patch vulnerable components. Lack of vulnerability management processes. Reliance on outdated or unsupported software. | Using components with known vulnerabilities refers to the practice of integrating libraries, frameworks, or other software components with known security flaws into an application. Attackers can exploit these vulnerabilities to compromise the application, steal data, or gain unauthorized access. |
OWASP Top 10 2024
OWASP Top 10 is a great place for developers and web security. Provides information about the most important security risks of web use. Let’s dive into OWASP Top 10 2024 by top 10 questions!
- Malicious Credential Use (M1)
- Security of Supply Chain Failure (M2)
- Insecure Authentication/Authorization (M3)
- Output Insufficient Validation (M4)
- Insecure Communication (M5)
- Inadequate Privacy Controls (M6)
- Insufficient Binary Protections (M7)
Malicious Credential Use (M1)
This risk identifies situations where credentials are misused, resulting in unauthorized access or other security measures.
Security of Supply Chain Failure (M2)
A weak supply chain can compromise the integrity of software products. The safety and security of the supply chain is important.
Insecure Authentication/Authorization (M3)
Weak authentication and authorization processes can expose your application to unauthorized access or privilege escalation.
Output Insufficient Validation (M4)
Failure to properly validate input/output can lead to vulnerabilities such as injection risk. Inadequate privacy controls can lead to information leaks or privacy breaches. Presented as part of the OWASP Global Application Security Conference to be held in September 2024.
Insecure Communication (M5)
Weak encryption, improper handling of sensitive data, and other communication-related issues pose significant risks.
Inadequate Privacy Controls (M6)
Protecting user privacy is crucial. Insufficient privacy controls can result in data leaks or privacy violations.
Insufficient Binary Protections (M7)
Lack of proper protections for binaries (executable files) can lead to exploitation.
Developers and security professionals should be aware of these risks to increase the security of their applications.
Queries About Vulnerabilities and Causes of OWASP Top 10 2023
- What is OWASP 10 standards?
The OWASP Top 10 is a standard that outlines the most critical security risks for web applications, providing guidance for developers and security professionals to prioritize their efforts in securing software. It serves as a globally recognized benchmark for assessing and mitigating web application vulnerabilities.
- What is OWASP full form?
OWASP stands for Open Web Application Security Project, an online community dedicated to improving software security. It offers resources, tools, and best practices for securing web applications against cyber threats.
- What are OWASP Top 10 proactive controls for?
The OWASP Top 10 Proactive Controls serve as guidelines for developers to build secure software from the ground up, emphasizing proactive measures to prevent common security vulnerabilities. They cover areas such as security architecture, secure coding practices, and effective security testing methodologies.
Hope you’ll enjoy this topic of Discover Vulnerabilities and Causes of OWASP Top 10 2023. We believe that our article about the Discover Vulnerabilities and Causes of OWASP Top 10 2023 will be understandable and useful for you. If you have questions or want to share, please feel free to leave a comment.
Thanks for visiting top 10 questions!